The most addictive game is "getting more games". Follow Wario64's discord, check prices at isthereanydeal, get the Epic freebies, mix and match bundles at Fanatical.
rotopenguin
Oh god, the design of classic game controllers were all war crimes lol
I think the best assurance is - even spies have to obey certain realities about what they do. Developing this backdoor costs money and manpower (but we don't care about the money, we can just print more lol). If you're a spy, you want to know somebody else's secrets. But what you really want, what makes those secrets really valuable, is if the other guy thinks that their secret is still a secret. You can use this tool too much, and at some point it's going to "break". It's going to get caught in the act, or somebody is going to connect enough dots to realize that their software is acting wrong, or some other spying-operational failure. Unlike any other piece of software, this espionage software wears out. If you keep on using it until it "breaks", you don't just lose the ability to steal future secrets. Anybody that you already stole secrets from gets to find out that "their secrets are no longer secret", too.
Anyways, I think that the "I know, and you don't know that I know" aspect of espionage is one of those things that makes spooks, even when they have a God Exploit, be very cautious about where they use it. So, this isn't the sort of thing that you're likely to see.
What you will see is the "commercial" world of cyberattacks, which is just an endless deluge of cryptolockers until the end of time.
hint
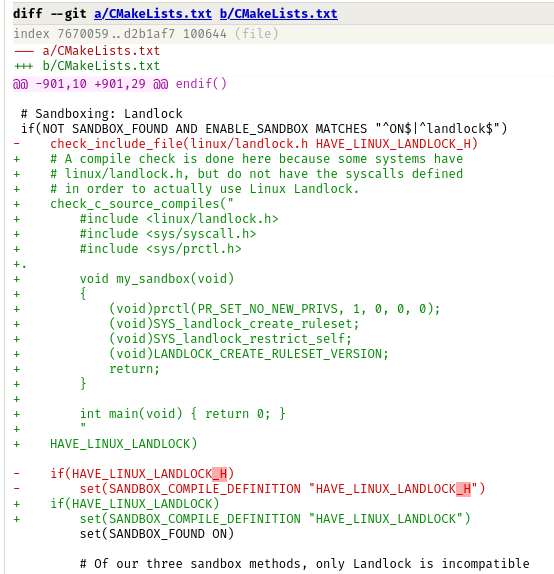
It is one singular character. Everything else is fine.
This is a sliver of one patch, there is a bug here that disabled a build tool that breaks the attack. Can you find it?
In the coming weeks, you will know if this attacker recycled any techniques in other attacks. People have furiously ripped this attack apart, and are on the hunt for anything else like it out there. If Jia has other naughty projects out here and didn't make them 100% from scratch, everything is going to get burned.
How do you know there isn't a logic bug that spills server secrets through an uninitialized buffer? How do you know there isn't an enterprise login token signing key that accidentally works for any account in-or-out of that enterprise (hard mode: logging costs more than your org makes all year)? How do you know that your processor doesn't leak information across security contexts? How do you know that your NAS appliance doesn't have a master login?
This was a really, really close one that was averted by two things. A total fucking nerd looked way too hard into a trivial performance problem, and saw something a bit hinky. And, just as importantly, the systemd devs had no idea that anything was going on, but somebody got an itchy feeling about the size of systemd's dependencies and decided to clean it up. This completely blew up the attacker's timetable. Jia Tan had to ship too fast, with code that wasn't quite bulletproof (5.6.0 is what was detected, 5.6.1 would have gotten away with it).
There's hardlink, and then below that there's the COW/dedupe version called "reflink". Two files can point to the same chunks of data (extents), and altering one does not alter the other. Two files can point to just some of the same chunks of data, too. I don't think there is much indicator for when this is happening, besides the free space vs used space accounting looking crazy. If you "compsize" two reflinked files at once, it'll show you the difference.
You can do "zfs style raid things" with btrfs, but there are way too many reports of it ending badly for my tastes. Something-something about "write hole".
compsize will give you an honest overview of what's going on with btrfs.

When I run virt-manager on Bookworm, all it does is tell me that "xen is not connected". There is nothing to indicate that KVM is anything that virt-manager might support, or why it currently doesn't.
The best I can do is to make a VM in gnome boxes, use "ps" to capture its command line to qemu, re-format that into something that I can put into a bash script, and edit in additional options that Boxes/libvirt absolutely refuse to support.
Most of the host integration features are better in Virtualbox. On the other hand, with qemu I don't have to look at VB filling the journal with ubsan errors (and wonder if its crappy driver is corrupting shit). If VB supported KVM, I would go right back to it.